In this Configure Cisco ASAv on GNS3 for Hands-on Labs, we delve into getting the most popular Cisco virtualised firewall ASAv in GNS3 step by step.
GNS3 labs must be rich and cover contexts of networking which gives great hands-on experience for the student and professional alike. Imagine being able to configure site-to-site vpns between your ASAv and a Cloud Instance, and being able to perform a myriad of tasks in order to understand how the real world expectation might be between the chosen technologies?
The beauty of scalability that comes with virtualised appliances in network design architectures to prove a concept or test and troubleshoot scenarios?
With the Cisco® Adaptive Security Virtual Appliance (ASAv), you have the flexibility to choose the performance you need for your business. ASAv is the virtualized option of our popular ASA solution and offers security in traditional physical data centers and private and public clouds. Its scalable VPN capability provides access for employees, partners, and suppliers—and protects your workloads against increasingly complex threats with world-class security controls.
Create the initial master template for your ASAv
Download the ASAv qcow2 file with the OS version of your choice from Cisco.com.
Open GNS3 and click on File > + New Template >
Select Firewalls from the GNS3 Appliances List
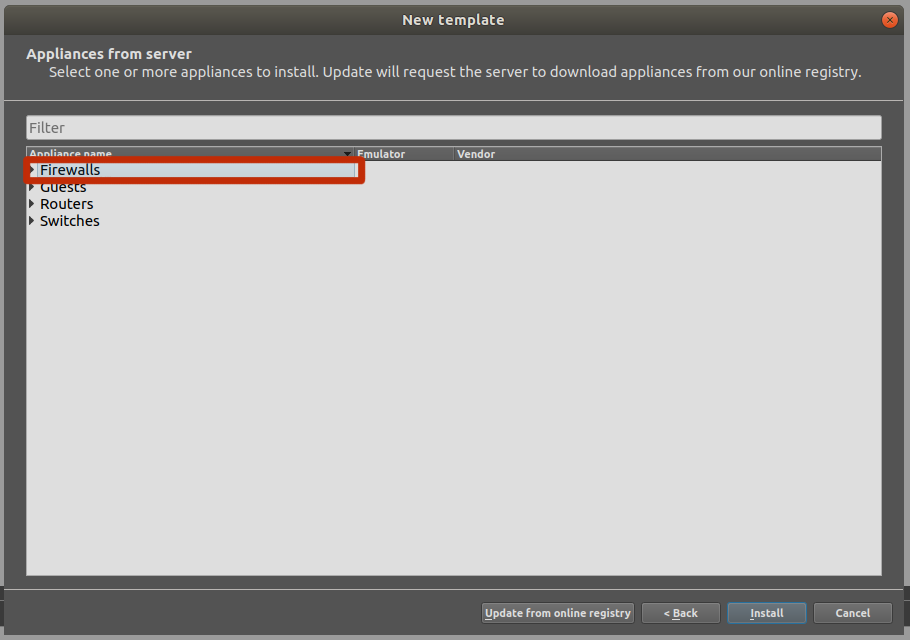
Install the Appliance on GNS3 VM as Recommended
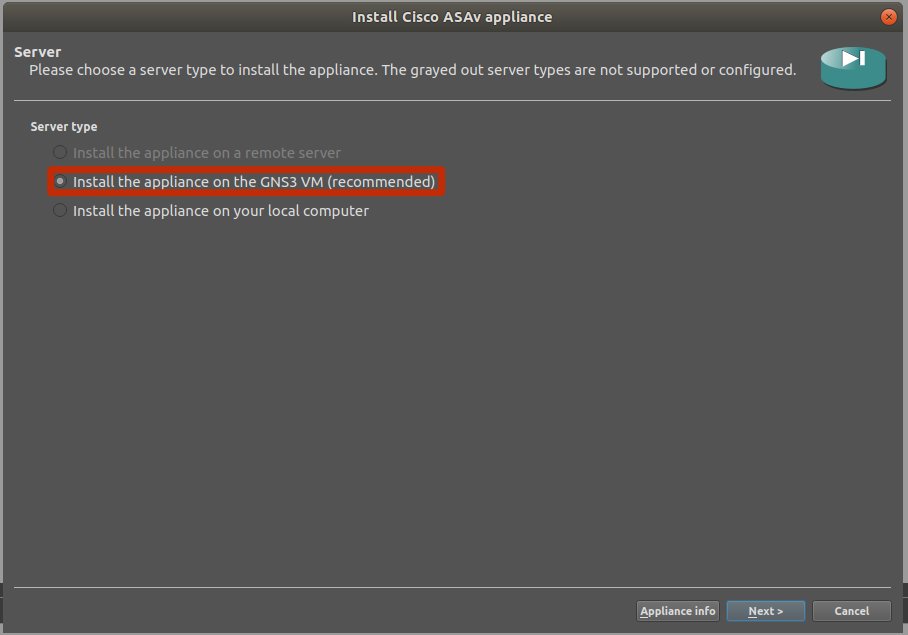
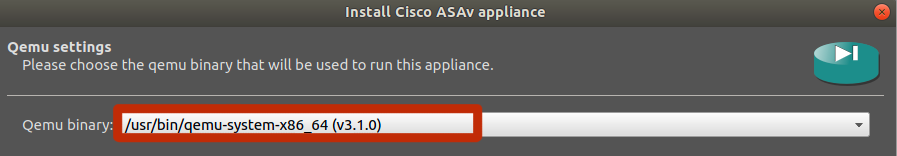
Choose “Default” for the VM type and hit next. Name the VM (ASAV 9.8.1 for example) and hit next. Select the x86_64 Qemu binary and set the RAM to 2048mb. Hit next.
Select ASAv Version and Install and Click Next
GNS3 would locally locate the downloaded *qcow2 appliance and populate the list for you to make a choice. Select your ASAv version and click Next.
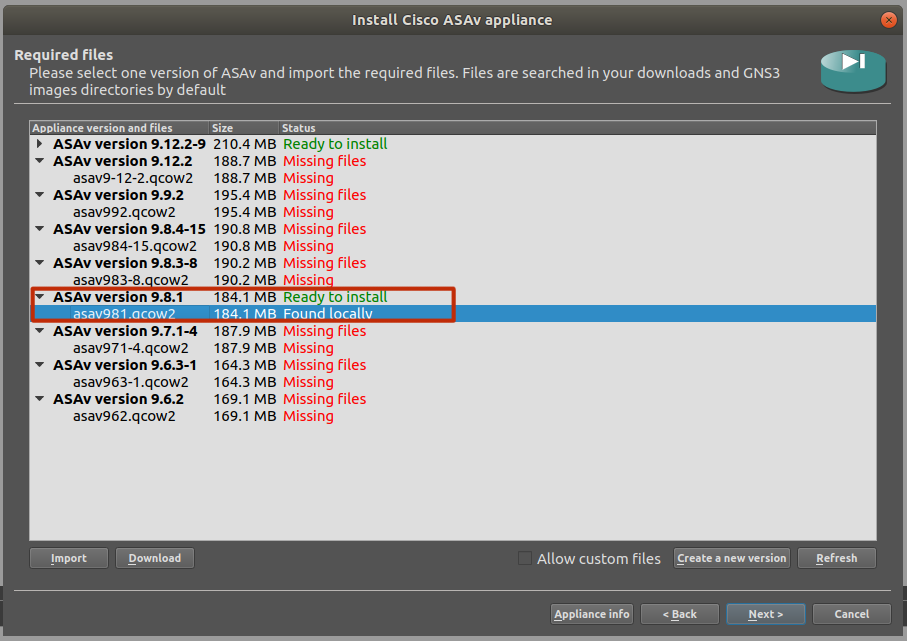
Click Next and Continue
It is a good idea to trial your idea with a single ASAv and once this has worked out well, apply it to the master template as the gold image for future replica ASAv firewalls.
Create a new GNS3 Project
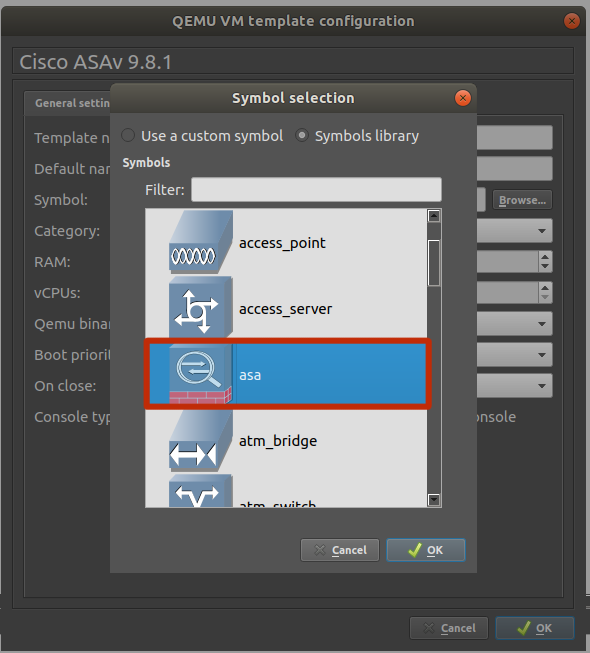
Right click on ASAv and change the symbol (this is an optional step)
Select Symbol for your ASAv,change the category to Security Devices, and set the console type to vnc. We will change this to telnet later in the guide as we apply this to our master ASAv appliance.
Select vnc from the drop down to set console type to vnc
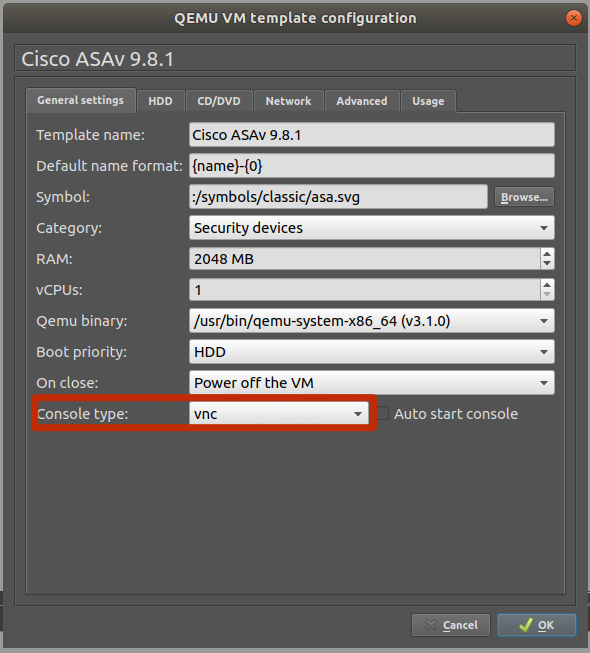
Uncheck Use as linked base VM(This is recommended initially until you’ve got it all working as should)
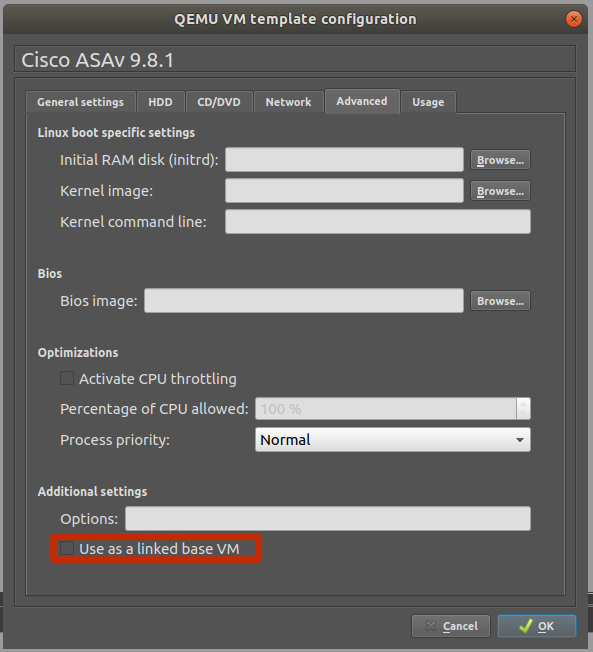
(It is recommended to perform all the necessary configurations before enabling this option which will make newer instances inherit the global settings. We shall do it as the final step once we get each bit done.)
Configure Cisco ASAv on GNS3 for Hands-on Labs
Start the ASAv and Click open with Console
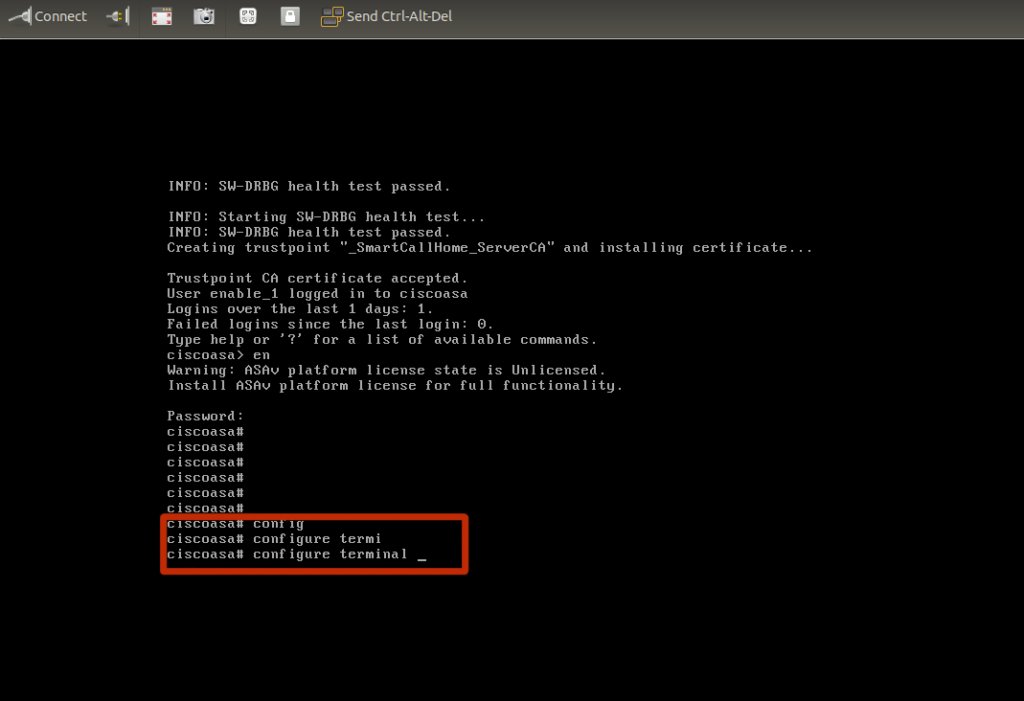
Set Telness Access: Follow steps below
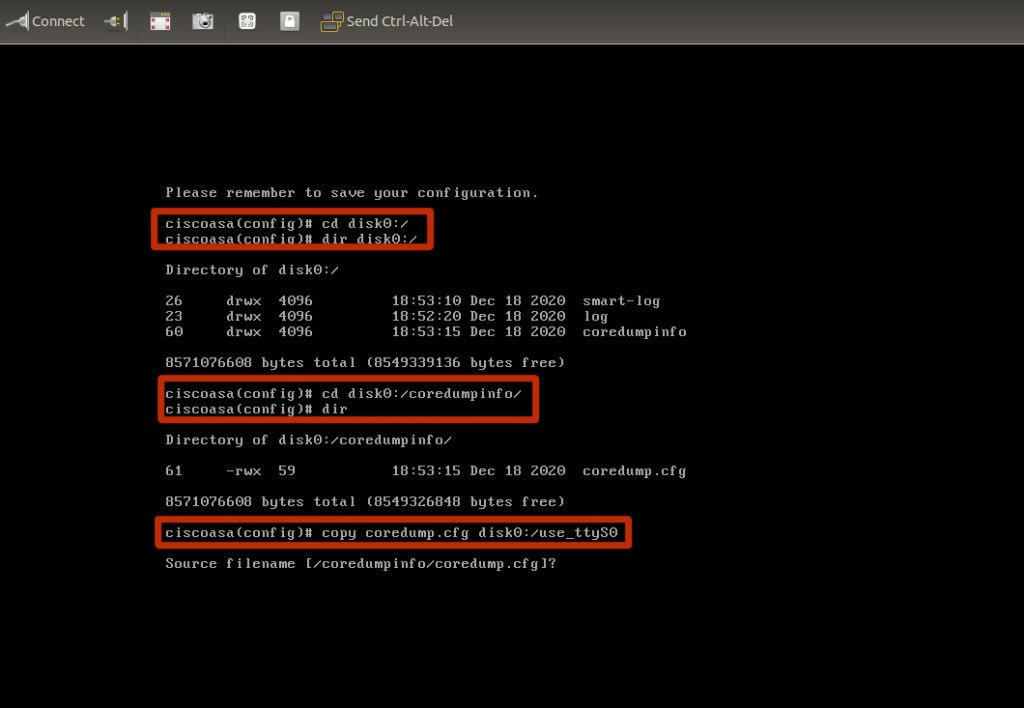
copy coredump.cfg from the coredumpinfo directory to disk0:/
ciscoasav#conf t ciscoasav#cd disk0:/coredumpinfo/ ciscoasav#copy coredump.cfg disk0:/use_ttyS0
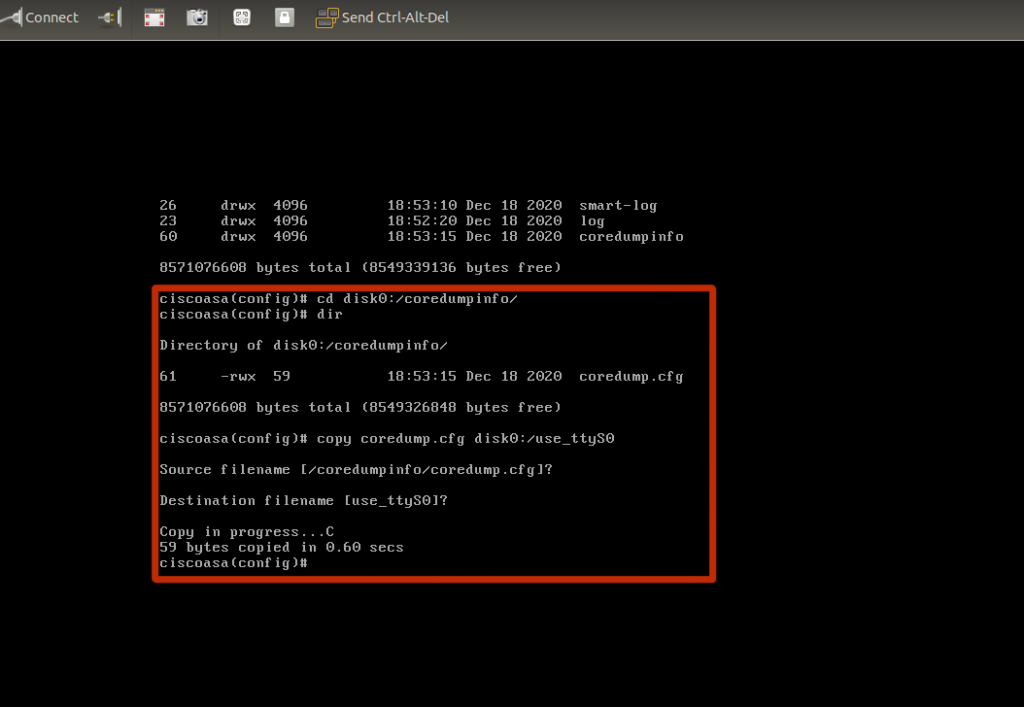
Verify you work (always check if what you did worked)
ciscoasav# dir disk0:/ Directory of disk0:/ 10 drwx 4096 07:29:52 Dec 18 2020 smart-log 8 drwx 4096 07:28:58 Dec 18 2020 log 11 drwx 4096 07:29:56 Dec 18 2020 coredumpinfo 7 -rwx 59 07:36:44 Dec 18 2020 use_ttyS0 1 file(s) total size: 59 bytes 8571076608 bytes total (8549355520 bytes free/99% free) ciscoasav#
Once the above steps are completed, go ahead and configure the master template. Now that we are happy that the telnet access works,
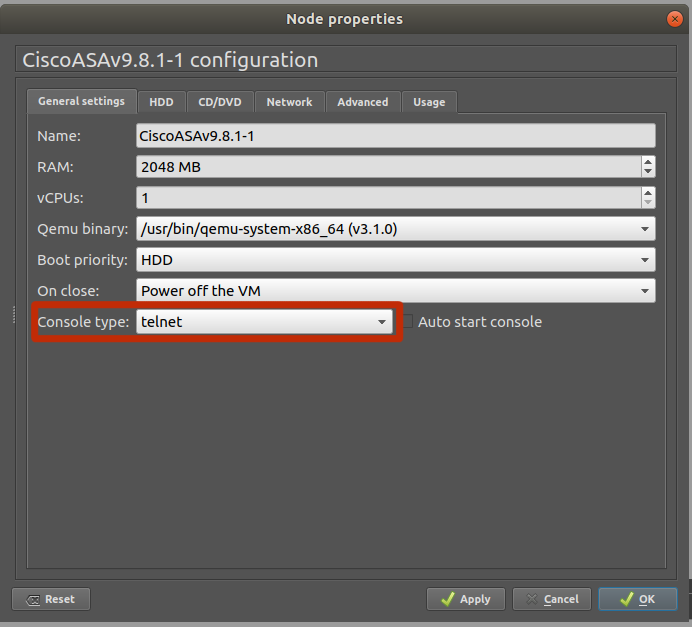
Set Console Type to Telnet
Now that you have set the use_ttyS0 on the ASAv, go ahead and power the ASAv off.
You must power the ASAv off to do this. You can change it with the device powered on, but you would encounter the error “No connection could be made because the target machine actively refused it”.
Click the Advanced settings tab. Uncheck the “Use as a linked base VM” box. We will check this later in the guide. Click OK then Apply > OK to save the device. This device will be configured as the “master template” for the ASAv.
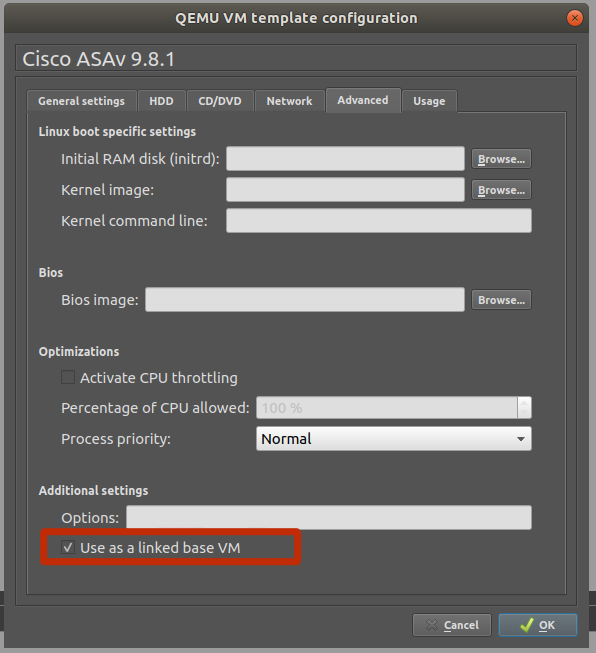
Configure the ASAv for telnet access
Close the preferences page, click Apply > OK to save the template.
Now that we have Cisco ASAv working exceptionally well in GNS3, let us now go into configuring a sample Cisco ASA 5506-X Deployment Topology.
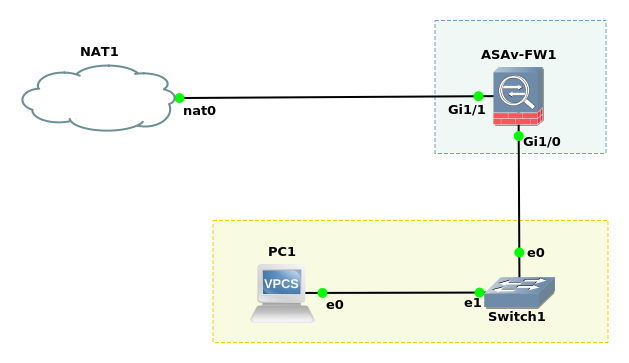
Figure 1.0 Sample Cisco ASA 5506-X Deployment Topology
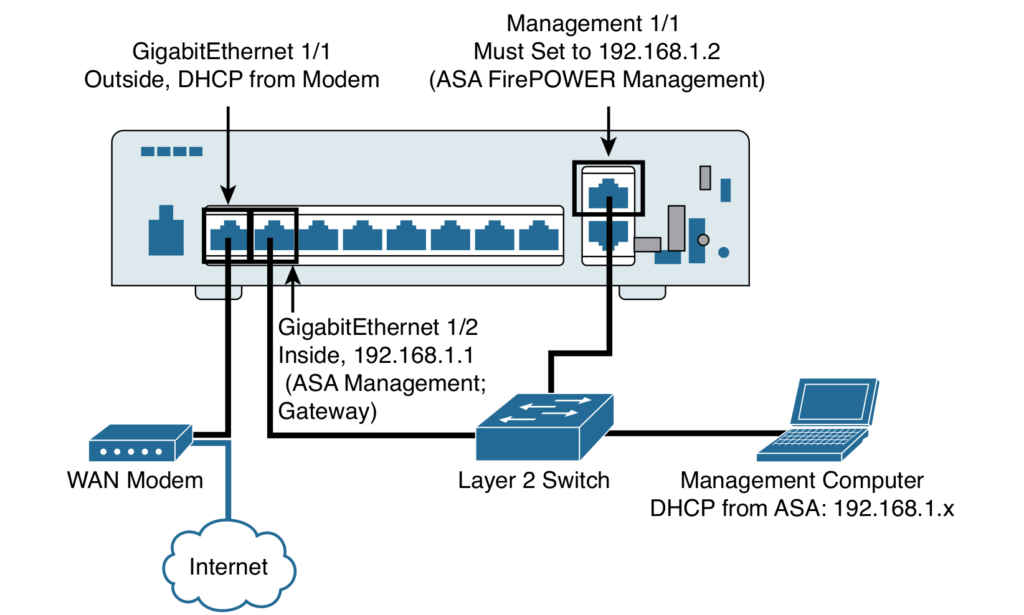
In this lab we shall Configure ASAv for the Internet using the following configuration sample.
Figure 1.1: ASA 5506-X Factory Default Configuration
!
interface GigabitEthernet1/0
nameif inside
security-level 100
ip address 192.168.1.254 255.255.255.0
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address dhcp setroute
!
!
dns domain-lookup outside
dns server-group DefaultDNS
name-server 8.8.8.8
name-server 8.8.4.4
object network obj_any
subnet 0.0.0.0 0.0.0.0
!
!
object network obj_any
nat (inside,outside) dynamic interface
route outside 0.0.0.0 0.0.0.0 8.8.8.8 1
!
!
dhcpd address 192.168.1.100-192.168.1.200 inside
dhcpd dns 8.8.8.8 8.8.4.4 interface inside
dhcpd enable inside
!
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map global_policy
class inspection_default
inspect icmp
!
Thanks for stopping by to read this article on how to Configure Cisco ASAv on GNS3 for Hands-on Labs. Below is a related article: How to Configure Cisco ASA 5506-X for Internet