What is Network Access Control (NAC) and How Does it Work?
Network Access Control (NAC) is a crucial component of modern-day network security that allows organizations to restrict access to their networks and systems to authorized users and devices. NAC helps to ensure that only trusted devices and users can access sensitive information, preventing potential security breaches and protecting critical data. In this article, we’ll take a closer look at what NAC is, how it works, and why it’s essential for organizations to implement it as part of their overall cybersecurity strategy.
What is Network Access Control (NAC)?
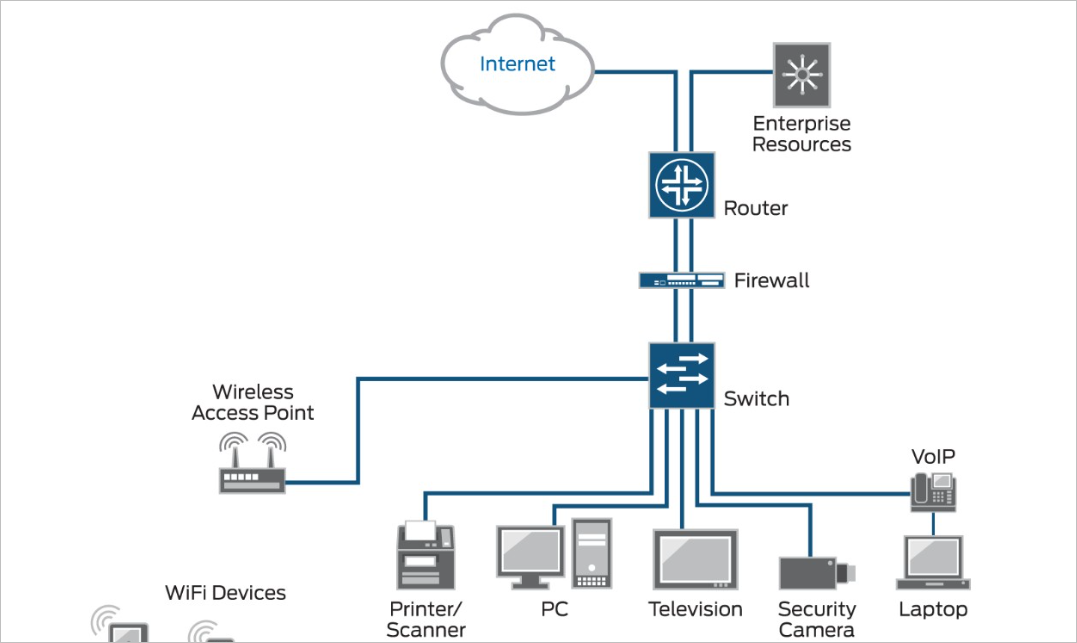
Network Access Control (NAC) is a security technology that controls access to network resources based on predefined policies. NAC systems are designed to verify the identity of devices and users attempting to access a network, ensuring that only authorized users and devices are granted access. NAC systems are typically deployed at the network’s edge, such as firewalls or switches, and are used to enforce security policies and restrict access to network resources.
How Does NAC Work?
NAC works by controlling access to network resources based on predefined policies. Before a device or user is granted access to a network, they must be authenticated and authorized. NAC systems use a variety of methods to verify the identity of devices and users, including digital certificates, biometric authentication, and two-factor authentication.
Once a device or user has been authenticated, the NAC system checks their compliance with security policies, such as antivirus software updates and patch management. If the device or user is compliant, they are granted access to the network. If not, they are denied access or placed in a quarantine zone until they can be brought into compliance.
Why is NAC Important for Organizations?
NAC is essential for organizations because it helps to ensure that only authorized users and devices can access their networks and systems. This is particularly important for organizations that handle sensitive data, such as healthcare providers, financial institutions, and government agencies.
NAC helps to prevent security breaches by ensuring that only trusted devices and users can access sensitive information. It also helps to enforce security policies and ensure that devices are up to date with the latest security patches and antivirus software updates.
Furthermore, NAC helps organizations to comply with regulatory requirements, such as HIPAA and PCI DSS. Compliance with these regulations is essential for organizations that handle sensitive data, and failure to comply can result in severe financial penalties and reputational damage.
Implementing NAC in Your Organization
If you’re considering implementing NAC in your organization, there are several factors to consider. First, you’ll need to assess your organization’s security needs and determine which NAC solution is best suited to your needs. There are several NAC solutions available, ranging from basic solutions to more advanced systems that integrate with other security technologies.
You’ll also need to consider your budget and the resources required to deploy and maintain your NAC solution. NAC solutions can be complex, and you’ll need to ensure that you have the necessary expertise and resources to manage your solution effectively.
In Conclusion
Network Access Control (NAC) is a critical component of modern-day network security that helps organizations to restrict access to their networks and systems to authorized users and devices. NAC helps to prevent security breaches, enforce security policies, and ensure compliance with regulatory requirements. Implementing NAC in your organization can be complex, but it’s essential for organizations that handle sensitive data and want to ensure that their networks and systems are secure.
Juniper has a very interesting article on the above subject.