IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server is an important element to networking in the real world. User location cannot be predicted as they may be at and out of a desk and up and about should they need to do so. Tying them to a local VLAN may only be helpful if they are bound to desks in those locations, although the most ideal outcome, it is not the most practical.
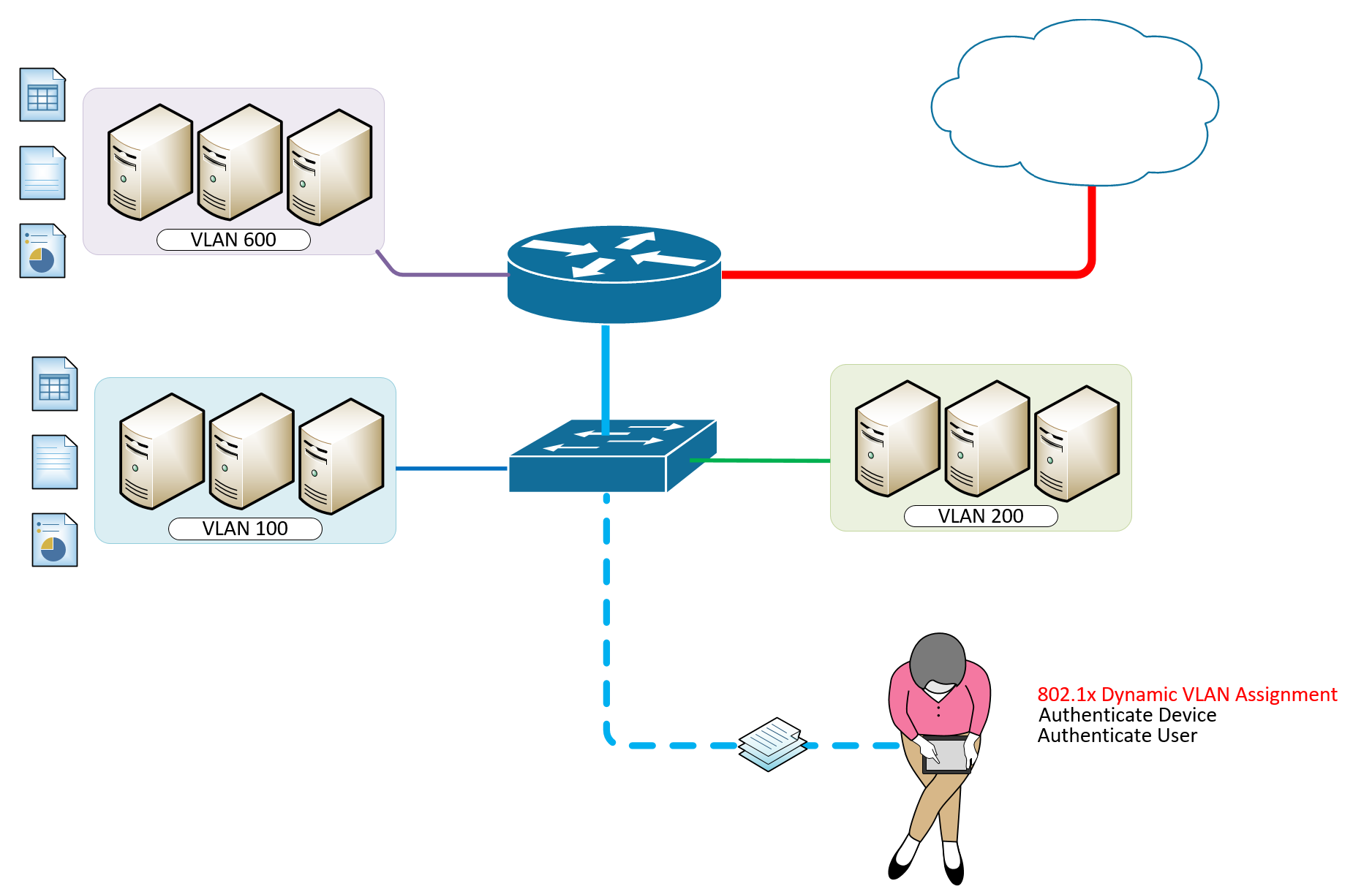
It is only wise to incorporate IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server in areas where you expect different teams to come to. Meeting rooms could for a moment have the accounting group or the development group meeting there and based on the intelligent and dynamic vlan assignmnet with 802.1x authentication, users port-access are defined their appropriate vlans for their respective access to resources on the network.
Open Lounge with IEEE 802.1X Authentication with Dynamic VLAN for all users to function as if they were at their own desks

How to Provision 802.1 X Authentication Step By Step With Dynamic VLAN Assignment With Windows Radius Server For 802.1x Clients.
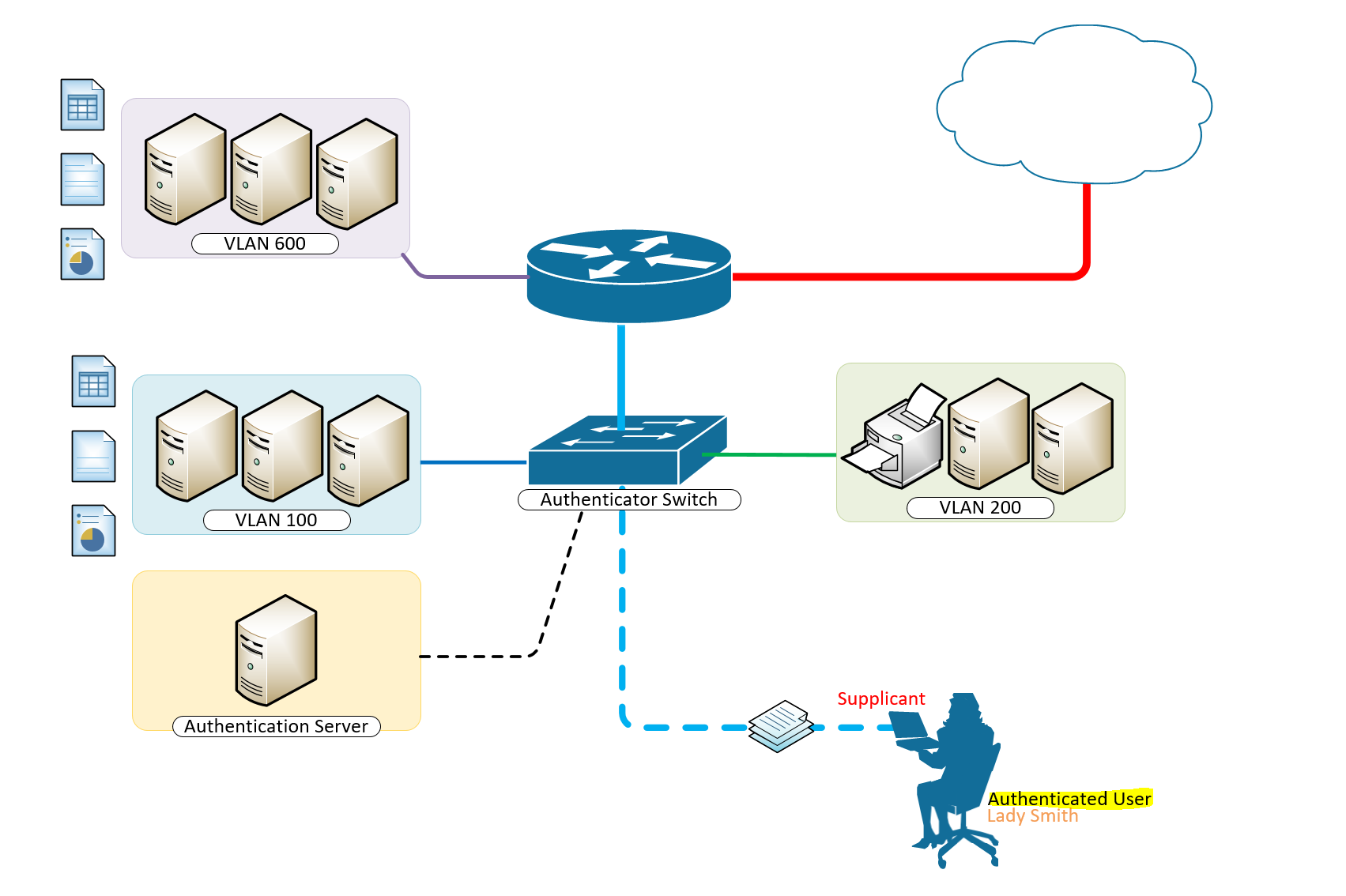
A typical configuration for a system under IEEE 802.1x Authentication control is shown in the following figure.
In this scenario, “Lady Smith” wishes to use services offered by servers on the LAN behind the switch. There are multiple VLANs with resources available based on user vlan membership. Her laptop computer is connected to a port on the Aruba 2920 Edge Switch that has 802.1x port authentication control enabled.
The laptop computer must therefore act in a supplicant role. Message exchanges take place between the supplicant and the authenticator which is the Aruba 2920 Switch, and the authenticator passes the supplicant’s credentials which is her (Windows Active Directory User Account Credentials) to the authentication server for verification. The NPS Server which is the authentication server then informs the authenticator whether or not the authentication attempt succeeded, at which point “Lady Smith” is either granted or denied access to the LAN behind the switch.
Setup Structure for IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
- Supplicant: Laptop running Microsoft Windows 10 or Windows 7
- Authenticator: HP Aruba 2920 Edge Switch
- Authentication Server: Microsoft NPS (Network Policy Server) running on Windows Server 2012 R2.
- User Database : Active Directory
For Windows Infrastructure
- Create NPS Server – Add Role on Windows Server 2012 R2
- Create DHCP Scopes for VLANS
- Create RADIUS Client on NAC using Network Policy Server
- Create Network Policies
- Configure a Network Policy for VLANs
- Start Wired Auto-Config Service
- Enable Network Authentication
Create NPS Server – Add Role on Windows Server 2012 R2
The Network Policy and Access Services allows you to define and enforce policies for network access authentication, authorisation, and client health using Network Policy Server(NPS), Health registration Authority(HRA), and Host Authorisation Protocol(HCAP).
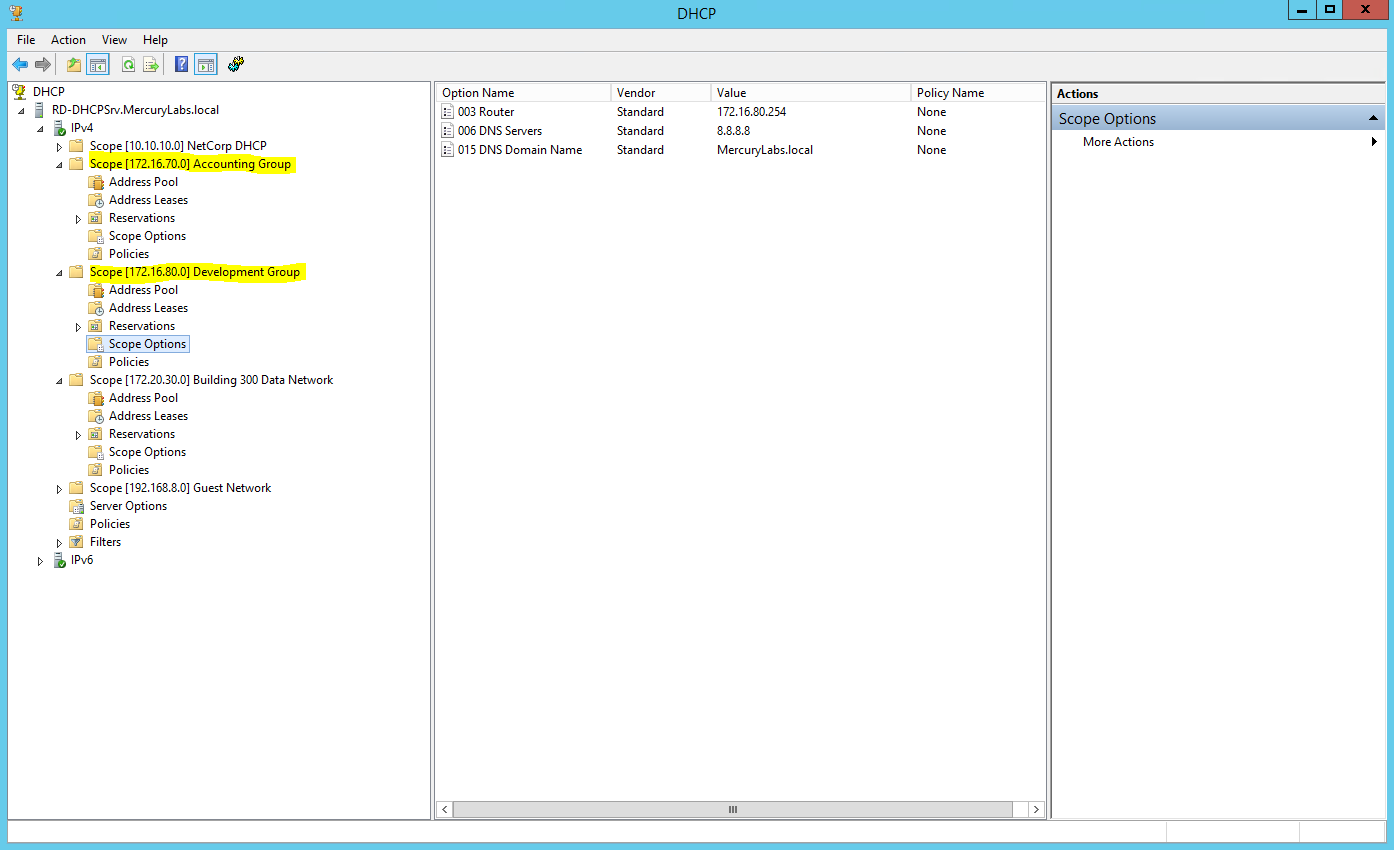
Create the DHCP Scopes for VLAN100 and VLAN200 Groups
- Development Group Scope – VLAN 100
- Accounting Group Scope – VLAN 200
SVI: ip address 172.16.80.254 255.255.255.0
Scope Subnet: 172.16.80.1/24
SVI:ip address 172.16.70.254 255.255.255.0
Scope Subnet: 172.16.70.0/24
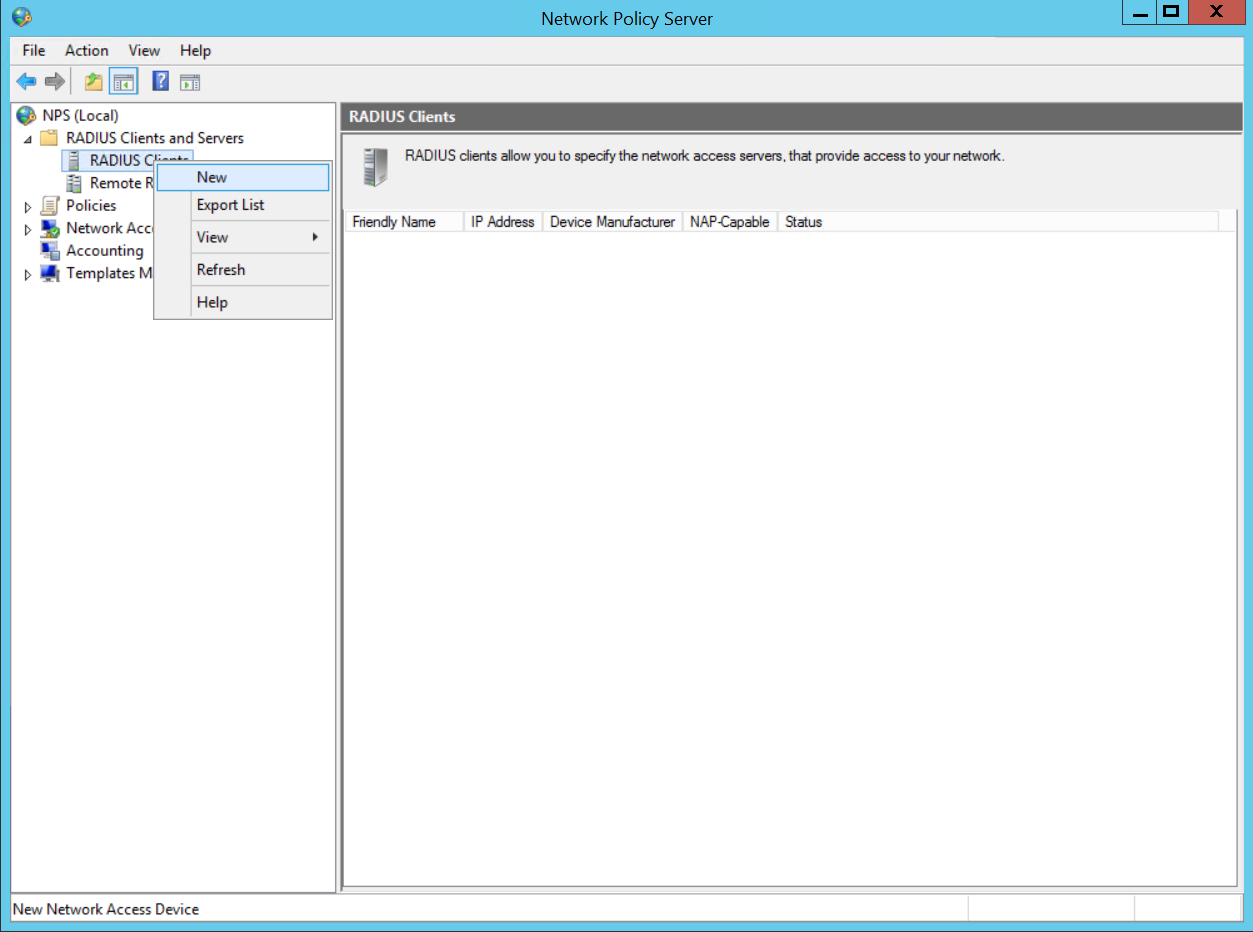
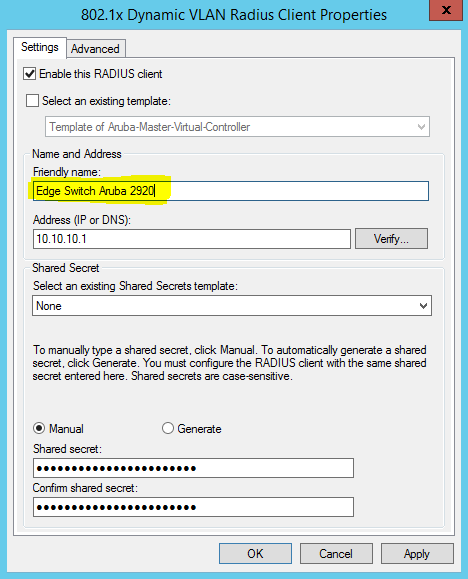
Create RADIUS Client on NAC using Network Policy Server
Secret Key:secret12
Add Edge Switch Management IP as the RADIUS Client
The Shared Secret Key: secret12 will be used in the Switch Configuration.
Create Network Policies for the Development Group and Accounting Department – Repeat same steps for the Accounting Department
![]()
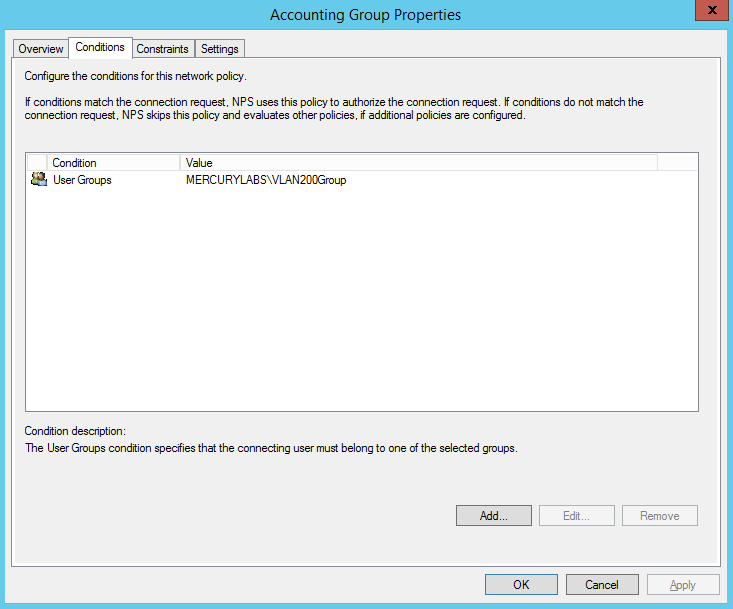
Create Network Policy for Accounting Group for VLAN 200
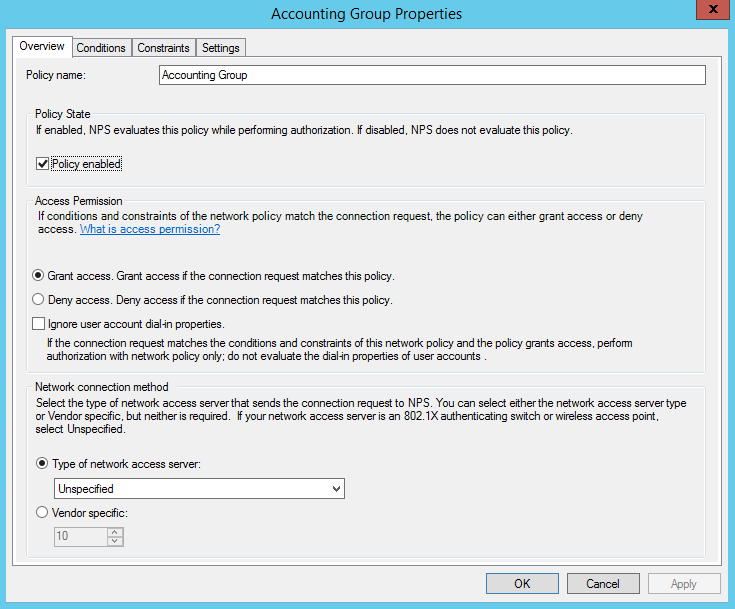
Create Network Policy Conditions for Accounting Group for VLAN 200
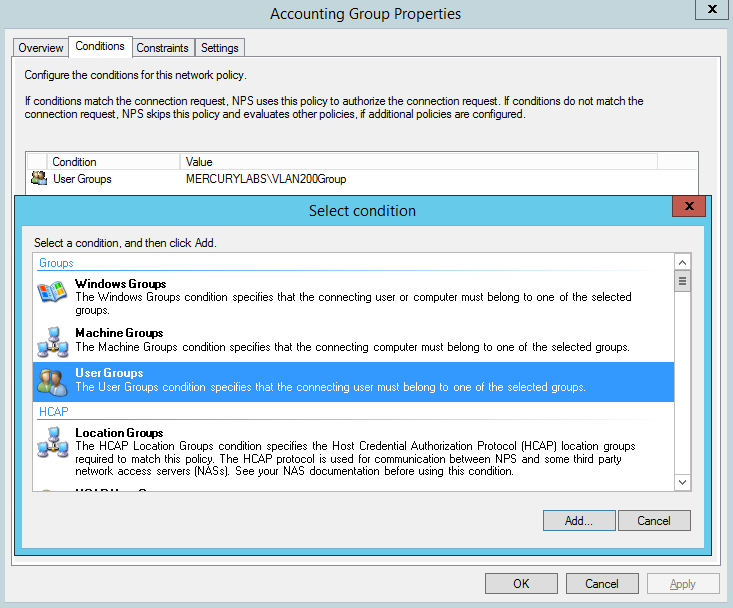
Create Network Policy Constraints for Accounting Group for VLAN 200
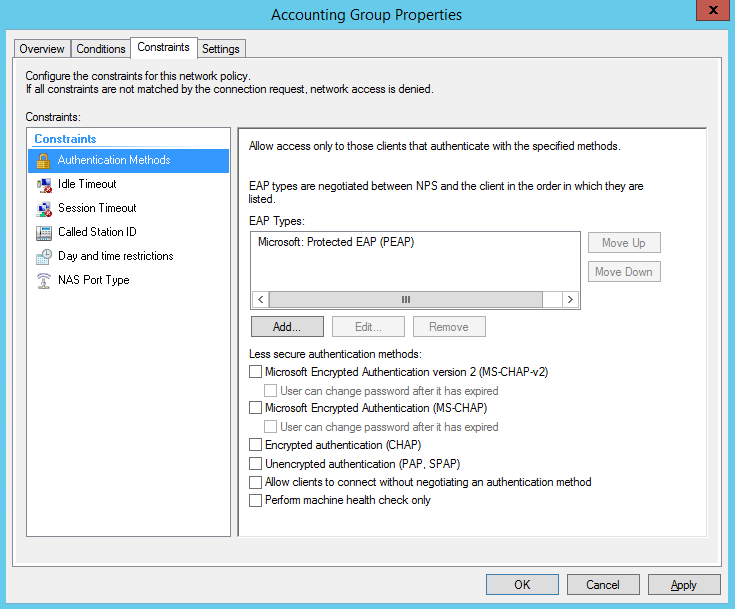
Create Network Policy Settings for Accounting Group for VLAN 200
Configuration Example
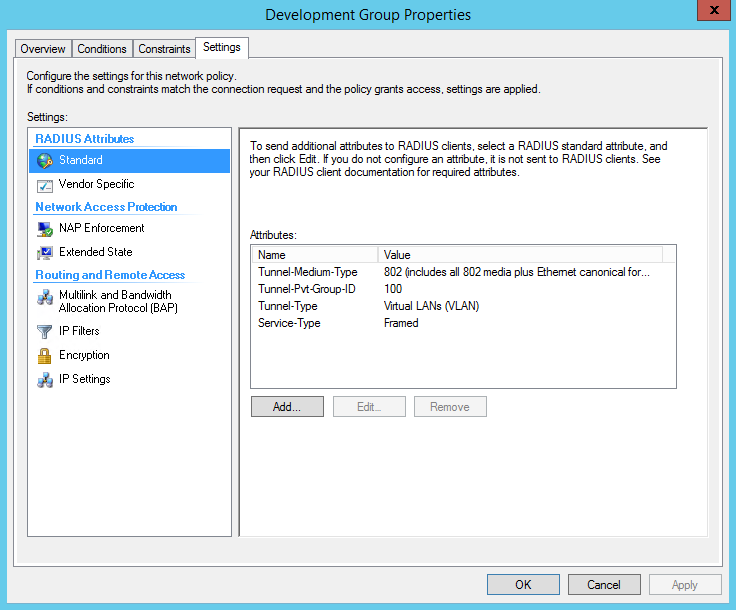
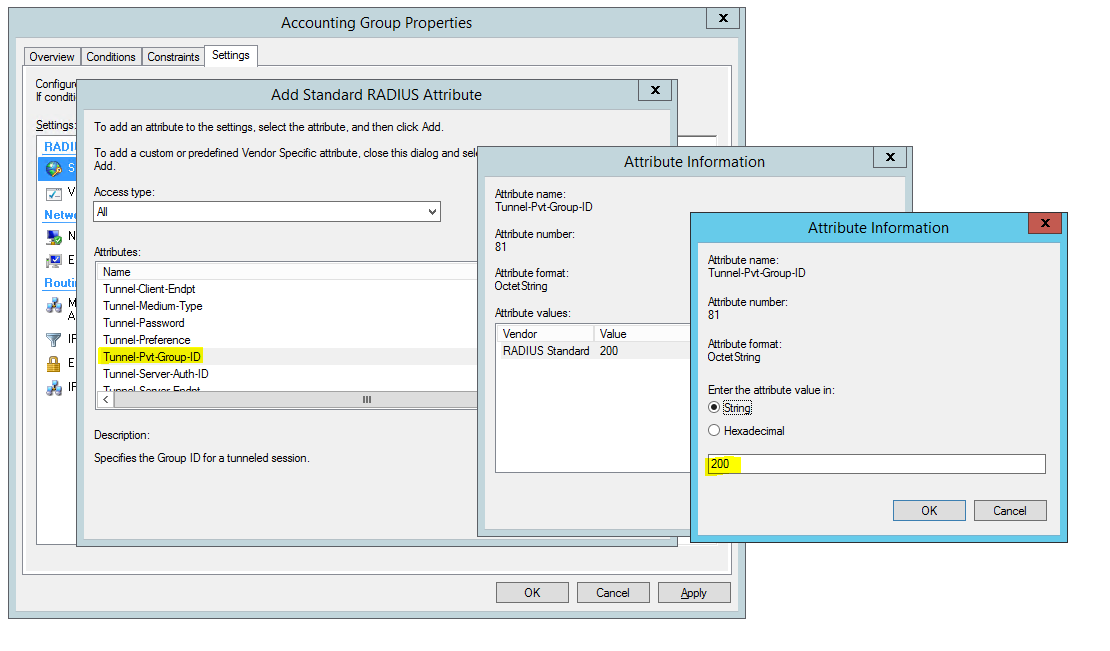
Here’s an example of how you might consider when configuring Microsoft NPS Server to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. This configuration has worked flawlessly on the HP Aruba 2920 Switch. The key to getting this to work is the use of a RADIUS element called: ‘Tunnel-PVT-Group-ID’. This is a RADIUS attribute that may be passed back to the authenticator (i.e. the Aruba 2920 Switch) by the authentication server (i.e. Microsoft NPS Server) when a successful authentication has been achieved. There are a few other elements which need to accompany it, but this is the key element, as it specifies the VLAN number that the user should be assigned to.
The other elements that need to be returned by the NPS Server are as follows:
Create Network Policy Settings forTunnel-PVT-Group-ID for VLAN 200
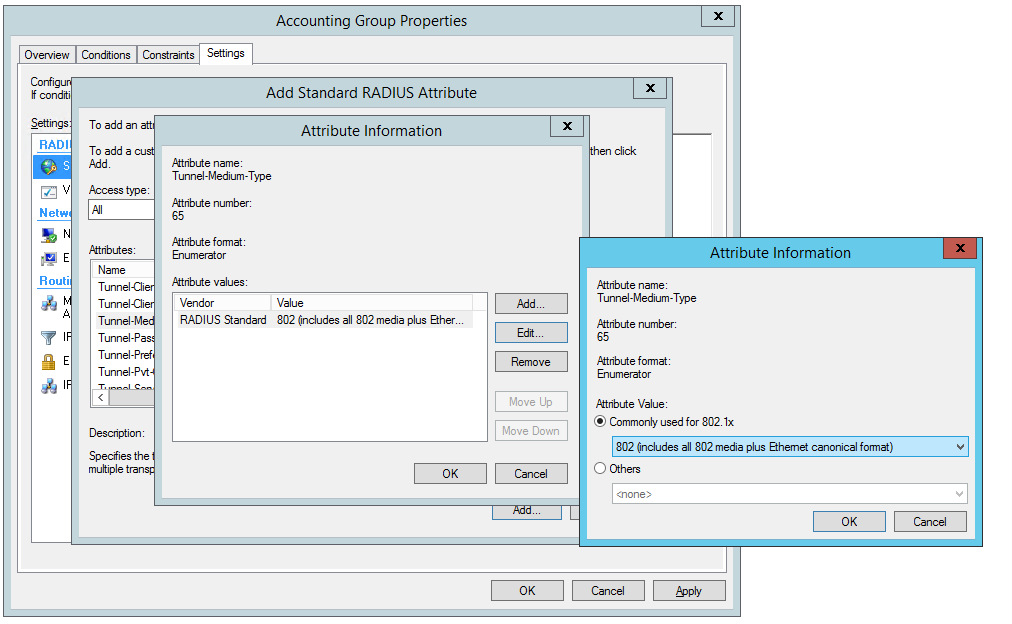
Create Network Policy Settings for Tunnel-Medium-Type for VLAN 200
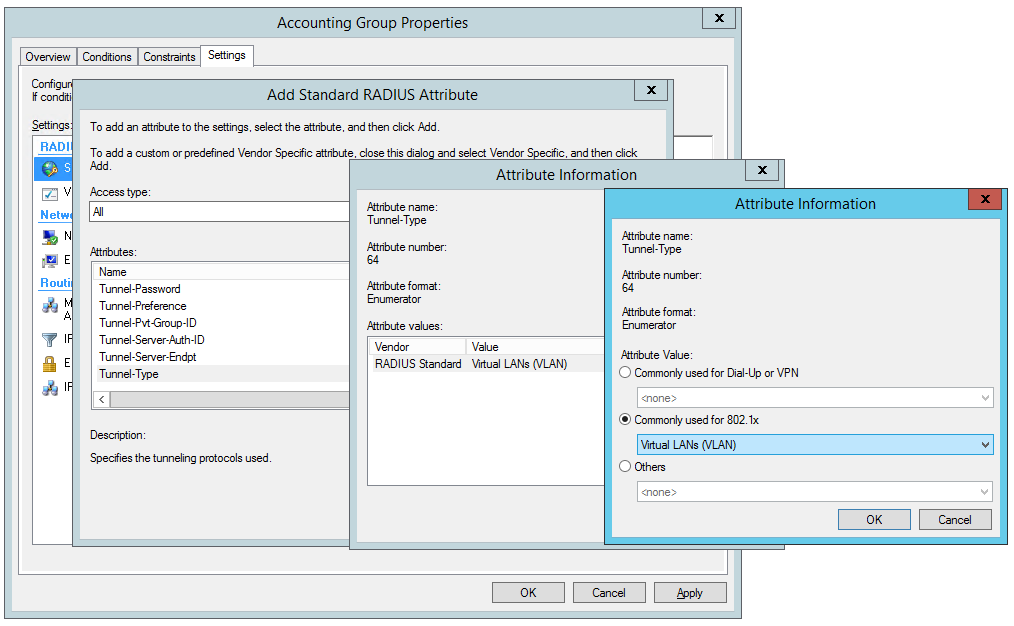
Create Network Policy Settings for Tunnel-Type for VLAN 200
For Client Infrastructure
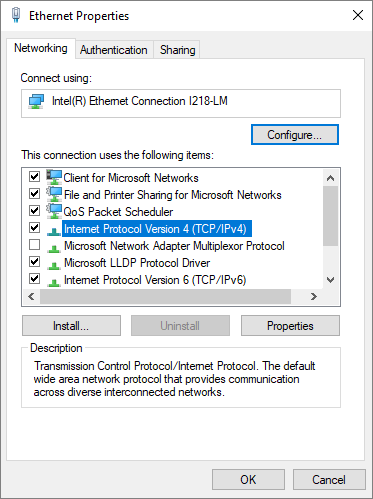
On the Supplicant, Windows 7 or 10 configure the following steps on the Ethernet Adapter to enable IEEE 802.1X Authentication
Configure Ethernet Authentication on Windows 7 or Windows 10 Operating System
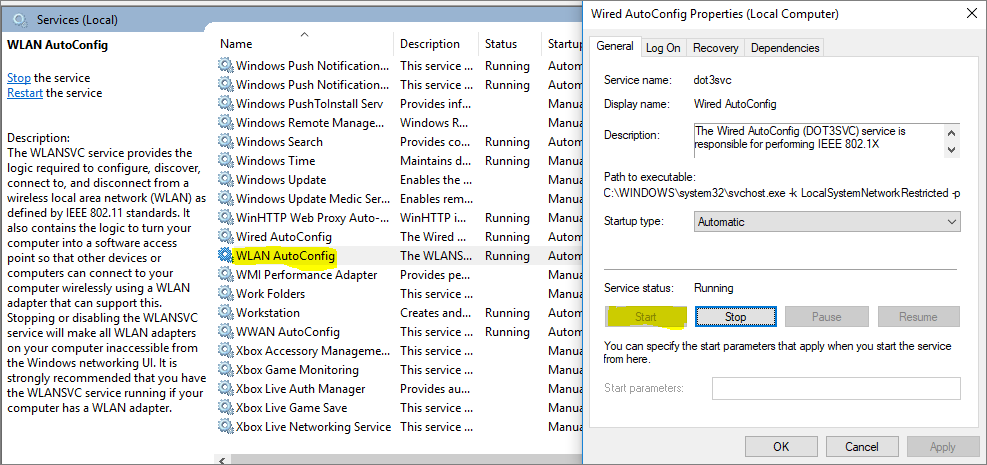
Enable IEEE 802.1X Authentication
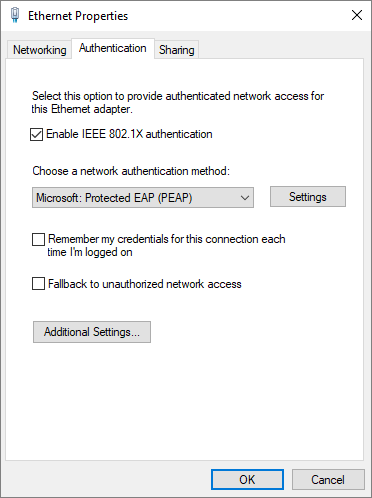
IEEE 802.1X Authentication – Advanced Settings
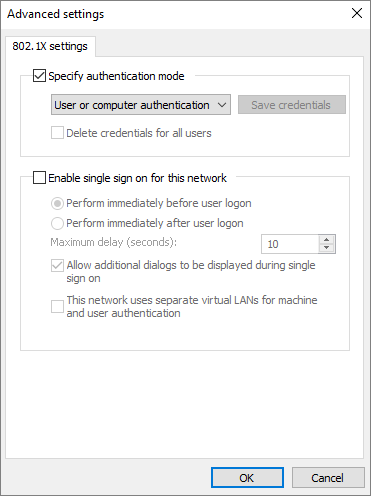
IEEE 802.1X Authentication – Protected EAP Properties
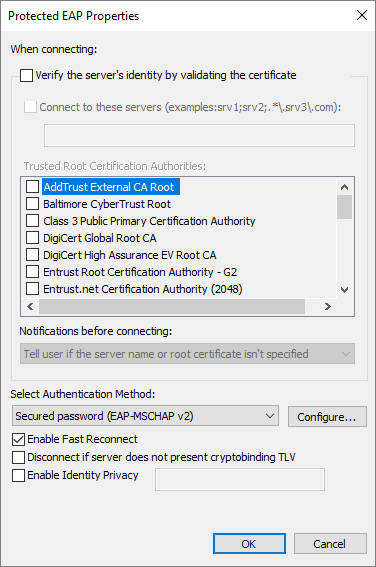
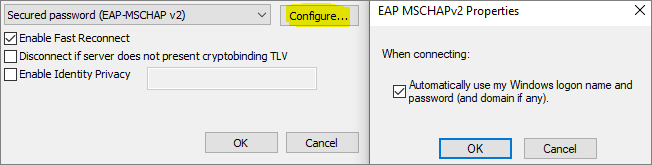
IEEE 802.1X Authentication EAP-MSCHAPv2 Properties
For Network Infrastructure
Connect Server Infrastructure to VLAN 400
vlan 400 name "Server Infrastructure" untagged 47-48 ip address 10.10.10.1 255.255.255.0 exit
Create VLAN for Accounting Group
vlan 200 name "Accounting Group" ip address 172.16.70.254 255.255.255.0 ip helper-address 10.10.10.40 exit
Create VLAN for Development Group
vlan 100 name "Development Group" ip address 172.16.80.254 255.255.255.0 ip helper-address 10.10.10.40 exit
Create AAA Configuration on Switch for Radius Authentication
hostname "Edge Switch Aruba 2920" radius-server host 10.10.10.10 key "secret12" aaa authentication port-access eap-radius aaa port-access authenticator 1-24 aaa port-access authenticator active
Download the Switch Configuration:
802.1 x wireless authentication step by step - Download the 802.1 x wired authentication step by step configuration sample
Test the IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
Verify Port-Access with the following user groups – VLAN 100 and VLAN 200
MacAuth(config)# show port-access authenticator
Port Access Authenticator Status
Port-access authenticator activated [No] : Yes
Allow RADIUS-assigned dynamic (GVRP) VLANs [No] : No
Auths/ Unauth Untagged Tagged % In RADIUS Cntrl
Port Guests Clients VLAN VLANs Port COS Limit ACL Dir Port Mode
---- ------- ------- -------- ------ --------- ----- ------ ----- ----------
1 1/0 0 200 No No No No both 1000FDx
2 0/0 0 None No No No No both 1000FDx
3 0/0 0 None No No No No both 1000FDx
4 0/0 0 None No No No No both 1000FDx
5 0/0 0 None No No No No both 1000FDx
6 0/0 0 None No No No No both 1000FDx
7 0/0 1 None No No No No both 1000FDx
8 0/0 0 None No No No No both 1000FDx
9 0/0 0 None No No No No both 1000FDx
10 0/0 0 None No No No No both 1000FDx
11 0/0 0 None No No No No both 1000FDx
12 0/0 0 None No No No No both 1000FDx
MacAuth(config)# show port-access authenticator
Port Access Authenticator Status
Port-access authenticator activated [No] : Yes
Allow RADIUS-assigned dynamic (GVRP) VLANs [No] : No
Auths/ Unauth Untagged Tagged % In RADIUS Cntrl
Port Guests Clients VLAN VLANs Port COS Limit ACL Dir Port Mode
---- ------- ------- -------- ------ --------- ----- ------ ----- ----------
1 0/0 0 None No No No No both 1000FDx
2 0/0 0 None No No No No both 1000FDx
3 0/0 0 None No No No No both 1000FDx
4 0/0 0 None No No No No both 1000FDx
5 0/0 0 None No No No No both 1000FDx
6 0/0 0 None No No No No both 1000FDx
7 1/0 0 100 No No No No both 1000FDx
8 0/0 0 None No No No No both 1000FDx
9 0/0 0 None No No No No both 1000FDx
10 0/0 0 None No No No No both 1000FDx
11 0/0 0 None No No No No both 1000FDx
12 0/0 0 None No No No No both 1000FDx
Think of what other clever things you can do from the information below;
Breakdown of Commands for RADIUS Authentication
#Define authentication host and pre-shared key. radius-server host 10.10.10.10 key "SpecifiedSharedSecretKey" #Enable processing of Disconnect and Change of Authorization messages from authentication server radius-server host 10.10.10.10 dyn-authorization #Set selected authentication mode aaa authentication port-access eap-radius #Configure specified ports for authentication aaa port-access authenticator 1-24 #Assign authenticated client VLAN to authenticator ports aaa port-access authenticator 1-24 auth-vid 200 #Assign unauthenticated client VLAN to authenticator ports aaa port-access authenticator 1-24 unauth-vid 999 #Activate authentication on assigned ports with configured options aaa port-access authenticator active exit
Verification Commands
VERIFICATION A number of CLI commands are available to verify authentication server and port access configuration, including: show port-access authenticator [port-list] [config | statistics | session-counters | vlan | clients [detailed]] show authentication show radius authentication show radius [host IP]
Thanks for reading. Please share your thoughts in the comment box below;